Understanding Zero Trust Architecture
As enterprises navigate the ever-shifting terrain of digital transformation, safeguarding network infrastructure and data has never been more critical. Zero Trust Network Access (ZTNA) is a compelling security framework in this panorama. But what is ZTNA, and why is it capturing widespread attention?
ZTNA represents a seismic shift in the way organizations approach security. The traditional notion of network security often relies on a well-defined perimeter, where entities within the boundary are implicitly trusted. However, this model is increasingly ineffective in the modern digital ecosystem characterized by cloud-based operations and remote workforces. ZTNA flips this paradigm by enforcing strict verification protocols for every user and device attempting to access a network, regardless of location.
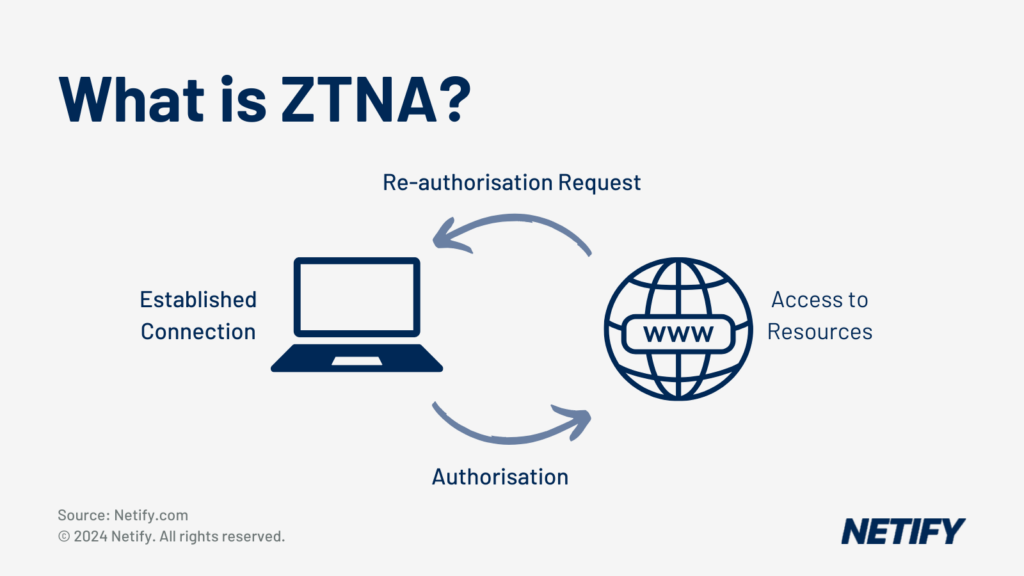
This approach stems from the philosophy of “never trust, always verify.” Unlike legacy systems, ZTNA doesn’t grant access based on location or past interactions. Instead, it continuously verifies credentials, building a trust model based on persistent authentication and authorization.
Core Components of ZTNA
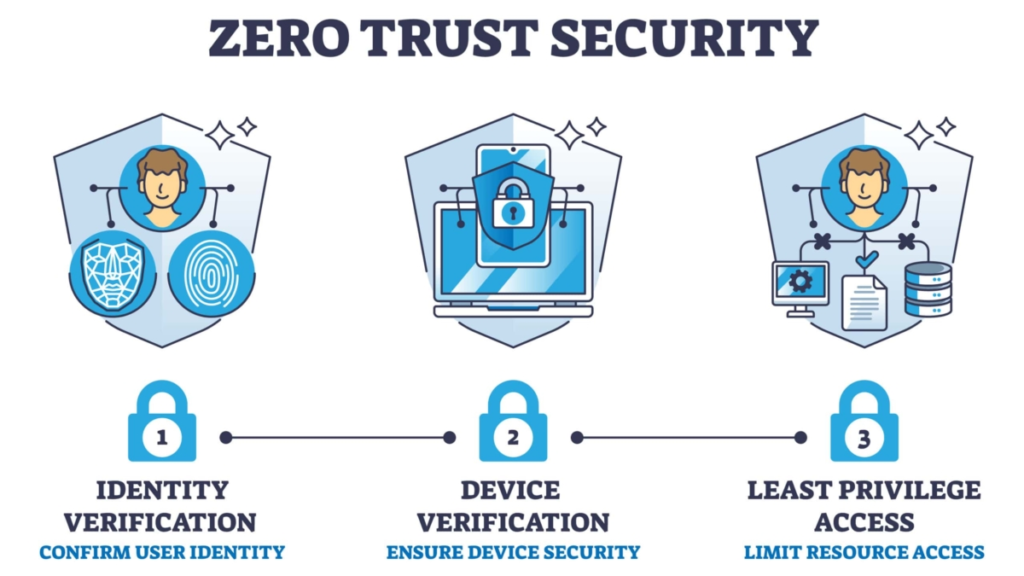
ZTNA’s architecture is anchored in several vital components, each contributing to its holistic security promise. Central to these components is the principle of identity verification. Users must authenticate themselves every time they seek access, and the system evaluates multiple factors—such as user credentials, contextual data, and device health—before granting authorization.
Moreover, ZTNA emphasizes the concept of “least privilege access,” which dictates that users only receive permissions necessary for task performance. This significantly mitigates the likelihood of internal threats and lateral movement within the network, frequently occurring before significant data breaches. Precise identity and access management (IAM) strategies, enhanced by strong endpoint security policies, constitute the foundation of Zero Trust Network Access (ZTNA).
This thorough approach starkly contrasts with traditional models, which primarily rely on perimeter controls and allow a wider network access spread once initial entry is granted. ZTNA’s granular approach ensures only essential access, guarding against unauthorized entry and potential exploitation of network resources.
Benefits of Implementing ZTNA
Adopting ZTNA substantially improves security posture, but its benefits extend beyond access control. The repeated verification processes inherent in ZTNA enhance security, making data breaches considerably harder to execute. By significantly minimizing implicit trust and introducing rigorous checks at every point, ZTNA effectively shrinks the attack surface that threat actors can exploit.
Additionally, ZTNA’s inherent design supports agility and flexibility, catering to the new-age demand for an increasingly remote workforce. This global workforce requires secure yet seamless access to organizational resources from diverse locations, which ZTNA facilitates without compromising the integrity of network defenses. It delivers robust security while maintaining operational dynamism and user satisfaction.
Organizations deploying ZTNA enjoy the advantages of heightened security, operational scalability, and cost efficiencies. With data protection laws becoming stricter, ZTNA helps businesses comply with regulatory requirements, reinforcing customer trust and corporate reputation in a competitive landscape.
Challenges and Considerations in Adopting ZTNA
While ZTNA’s merits are enticing, its implementation is not without hurdles. One prominent challenge is resistance to change. Shifting from a traditional security model to ZTNA demands alterations in mindset and operational practices, which many organizations may find daunting.
The deployment process can be complex, involving integrating current infrastructure with new ZTNA protocols. Adequate change management strategies must be employed, coupled with detailed training sessions, to empower IT staff to navigate and manage the new architecture effectively.

Understanding the transitionary complexities and committing to addressing them through strategic planning and education can significantly ease the adoption process. Organizations must weigh these challenges against the robust security and flexibility ZTNA offers to appreciate its value proposition fully.
Real-World Applications of ZTNA
ZTNA’s applications are diverse and helpful in the healthcare, finance, and retail industries. The healthcare sector, for instance, often deals with sensitive patient data that requires stringent protection measures. ZTNA helps secure this data, offering peace of mind to caregivers and compliance with healthcare regulations.
In the financial industry, ZTNA protects real-time transactions and vast stores of confidential client information. Financial institutions can fortify their operations by ensuring only verified access to prevent breaches or unauthorized data exposure. A pertinent example involves a leading retail organization that harnessed ZTNA to protect its digital landscape, seeing a marked decline in cyber incidents post-implementation.
These examples highlight how strategic deployment of ZTNA can enhance security outcomes across multiple domains, supporting specific operational needs while safeguarding critical assets.
ZTNA vs. VPN: A Comparative Analysis
ZTNA is often evaluated alongside virtual private networks (VPNs), which serve as mechanisms to secure remote connectivity. However, they differ significantly in execution. VPNs create secure tunnels for connecting remote users to the network but tend to apply generalized access measures, often resulting in network congestion and potential vulnerabilities.
In contrast, ZTNA employs a more refined approach by focusing on the user rather than the device location. Implementing identity-based access and continuous verification checks provides tailored security without compromise. This suits the demands of modern enterprises requiring granular access without straining network capacity.
While both ZTNA and VPNs have their merits, the former offers more resilience, making it an attractive option for future-looking organizations keen to advance their security infrastructure without encumbering network resources.
Future Trends in Network Security
As digital landscapes evolve, new trends in network security are emerging, bringing innovations like AI-driven analytics and machine learning into the fray. ZTNA is at the forefront of these evolutions and is set to transform enterprise security protocols significantly.
AI and machine learning enhance ZTNA by enabling proactive threat identification and response capabilities. This dynamism allows enterprises to strengthen their security infrastructure and create adaptive systems capable of evolving alongside emerging threats. Consider reviewing Forbes’ take on significant IT trends for a broader perspective.
Strategies for Successful ZTNA Implementation
Embarking on a ZTNA journey requires careful strategizing and implementation finesse. An exhaustive current-state analysis forms the bedrock of strategic planning, helping identify infrastructure gaps and seamlessly guiding the transition process.
Implementing in stages, through pilot programs or phased rollouts, can refine strategies, ensure stakeholder buy-in, and minimize disruption. Aligning ZTNA deployment with business goals and maintaining open communication channels among all vested parties enhances the likelihood of successful integration.
For actionable guidance and insights into implementing Zero Trust effectively, refer to Security Magazine’s comprehensive guide. Through practical steps, organizations can unlock the full potential of ZTNA, reinforcing their defenses while supporting strategic objectives.

